A BSCP (Burp Suite Certified Practitioner) review
Thursday 9th March 2023
After a couple of months of on-off practice, I can finally say I am a Burp Suite Certified Practioner. It was a fun exam and undoubtedly challenging in places. It was also my first security-related exam, so here's what it was like.
What is it?
PortSwigger released the BSCP exam to allow you to demonstrate the following:
Detect and prove the full business impact of a wide range of common web vulnerabilities.
It involves defeating two live web applications, each with three stages. You must first compromise a standard user account, then escalate to a privileged/root account and finally access a file on the host system. They have to be achieved in that order. You can't go straight to trying to compromise an admin account.
Each stage is vulnerable to one type of exploit (XSS, CSRF, SQLi, etc...), which is randomized with each exam attempt, somewhat prohibiting you from brute-forcing it. It's an open book, so you can refer to whatever notes you like. As you can see from The Academy, the range of potential vulnerabilities you may have to defeat is large. I encountered some of the following:
SQL Injection
OS Command Injection
DOM-based
Session Stealing
Host Header attacks
Cache Poisoning
more can be found here https://portswigger.net/web-security/all-materials...
You have 4 hours to do it in. ⏰
The Academy.
To prepare for the exam, PortSwigger provides The Academy. A collection of 300+ labs, each deliberately vulnerable to demonstrate a type of attack. They are broken down into Apprentice, Practitioner and Expert. PortSwigger recommends obtaining a Practioner level before attempting the exam. However, I and most other reviews I have read didn't bother getting to this level.
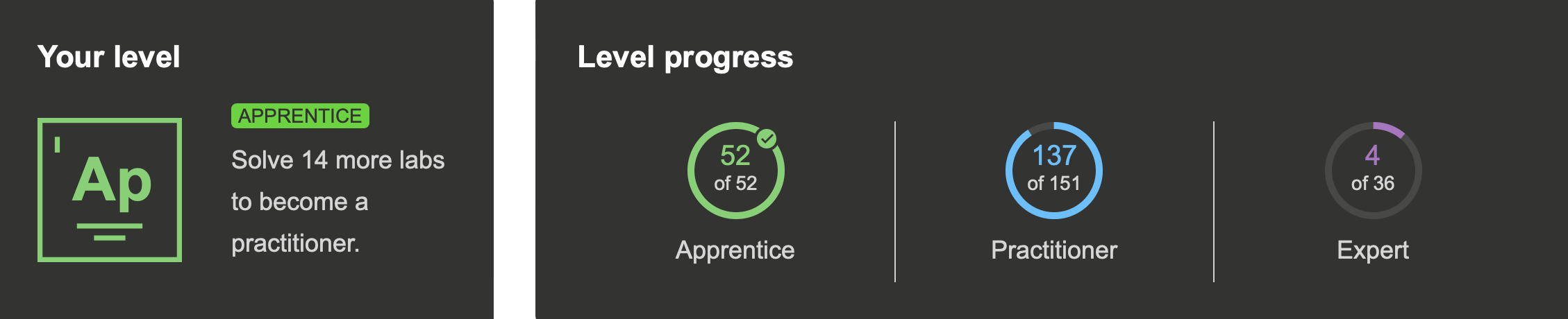
I must give kudos to PortSwigger for The Academy. I've been a software engineer for a while but never had to focus explicitly on security, so these tutorials helped me gain some instrumental knowledge. The labs also gave me a certain level of confidence that I could identify and exploit them in a sort-of real work scenario.
Initial Attempts.
I have to admit, right off the bat, that I didn't pass this first time. I got it on the 3rd attempt, unfortunately.
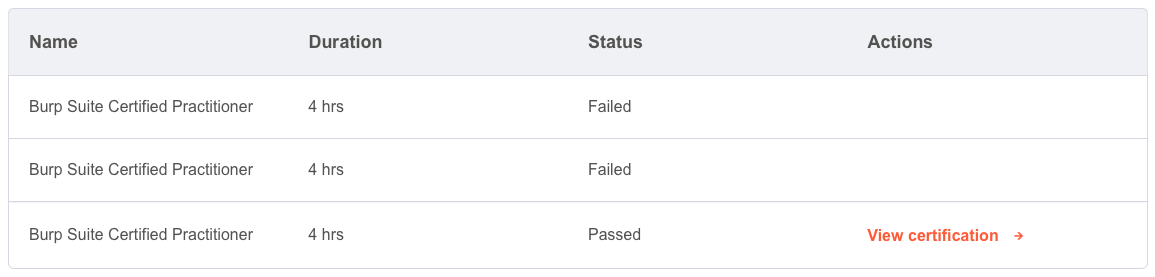
My first attempt got me to 5/6 with an hour to go. I fell on an OS command injection vulnerability, which Burp's Scanner picked up, but I failed to exploit it correctly. On the second attempt, I got to 3/6, with around 2 hours to go, and got stuck on what I suspect was a DOM-based exploit.
As I mentioned earlier, the exploits used in the exam are (supposedly) random, but I did get some repetition. Ironically, my 2nd failed attempt had one app precisely the same as my first attempt. But on my 3rd attempt, there were some fresh vulnerabilities.
Third Time Lucky
I started my 3rd attempt at 7 am, knowing I needed to give up for a while if I didn't do it now. It was also becoming fairly costly.
I got the 1st application done in about an hour and a half, again encountering some vulnerabilities I'd seen before. I then got stuck on gaining admin access on the 2nd application. I was at the point of giving up when I started trying anything and everything - seeing what would stick. This is where being in an exam environment is beneficial, as doing this against real-life targets would easily be detected. In the remaining 30 minutes, I got admin access by passing incorrect values to an endpoint, generating a correctly-signed cookie with an incorrect username. Finally, I encountered a fairly straightforward OS command injection exploit, just managing to submit the solution with about 10 minutes to spare.
Thoughts
It was challenging. Partly because I am not used to exams or the process. I was nervous to start with and had delayed taking the exam in the first place because of this. Secondly, there is an element of urgency in this exam. You can, and I did, go down rabbit holes thinking you've identified an exploit, which turns out to be incorrect. Burp's Scanner saved me on one, pointing out something I had missed.
Key lessons learned were:
The answer will be in the PortSwigger docs. I would have passed my first attempt if I'd just read a little more on OS Command Injection.
Don't give up, keep trying (harder). I was about to give up on my 3rd attemp, but perserveered and just about managed to crack it. This is a life lesson, really, not just about this exam.
Certain types of exploits only apply to specific stages in this exam (probably). For example, command injection probably won't be used to steal a session cookie, but it is helpful in obtaining the final solution file. So before you start the exam, have a rough idea of what vulnerabilities could be useful at each stage.
Stealing data through Host Header and Cache Poisoning attacks came up a few times. Know how to do that.
I wish you got a breakdown of what vulnerabilities you were presented with, as on my 2nd attempt, I am 90% certain what it was, but it would have been nice to know for sure.
This was an excellent addition to my skills as a Software Engineer developing web applications, both front and backend. Seeing a few job adverts on LinkedIn asking for the BSCP alongside OSCP and other industry-standard certifications was nice. Even if you don't feel like taking the exam, the labs offered by PortSwigger are great to mess around in and hone your skills.
Speaking of which, back to OffSec and preparing for the OSCP!